Linux procedure services bug provides root on all significant distros, exploit unveiled
3 min read

A vulnerability in Polkit’s pkexec component recognized as CVE-2021-4034 (PwnKit) is existing in the default configuration of all main Linux distributions and can be exploited to acquire total root privileges on the program, scientists warn right now.
CVE-2021-4034 has been named PwnKit and its origin has been tracked to the original commit of pkexec, more than 12 yrs ago, that means that all Polkit variations are afflicted.
Section of the Polkit open-source software framework that negotiates the conversation among privileged and unprivileged processes, pkexec permits an licensed user to execute instructions as a further person, doubling as an different to sudo.
Quick to exploit, PoC predicted before long
Researchers at Qualys details security enterprise located that the pkexec software could be made use of by nearby attackers to increase privileges to root on default installations of Ubuntu, Debian, Fedora, and CentOS.
They alert that PwnKit is very likely exploitable on other Linux running programs as effectively.
Bharat Jogi, Director of Vulnerability and Risk Investigation at Qualys points out that PwnKit is “a memory corruption vulnerability in Polkit’s, which lets any unprivileged user to acquire full root privileges on a susceptible method employing default polkit configuration,”
The researcher notes that the concern has been hiding in simple sight considering the fact that the initial model of pkexec inn May perhaps 2009. The online video beneath demonstrates the exploitability of the bug:
Exploiting the flaw is so quick, the scientists say, that proof-of-thought (PoC) exploit code is envisioned to turn into public in just a couple of times. The Qualys Research Crew will not launch a PoC for PwnKit.
Update: An exploit has already emerged in the general public space, fewer than a few hrs following Qualys released the complex information for PwnKit. BleepingComputer has compiled and analyzed the obtainable exploit, which proved to be reputable as it gave us root privileges on the procedure on all tries.
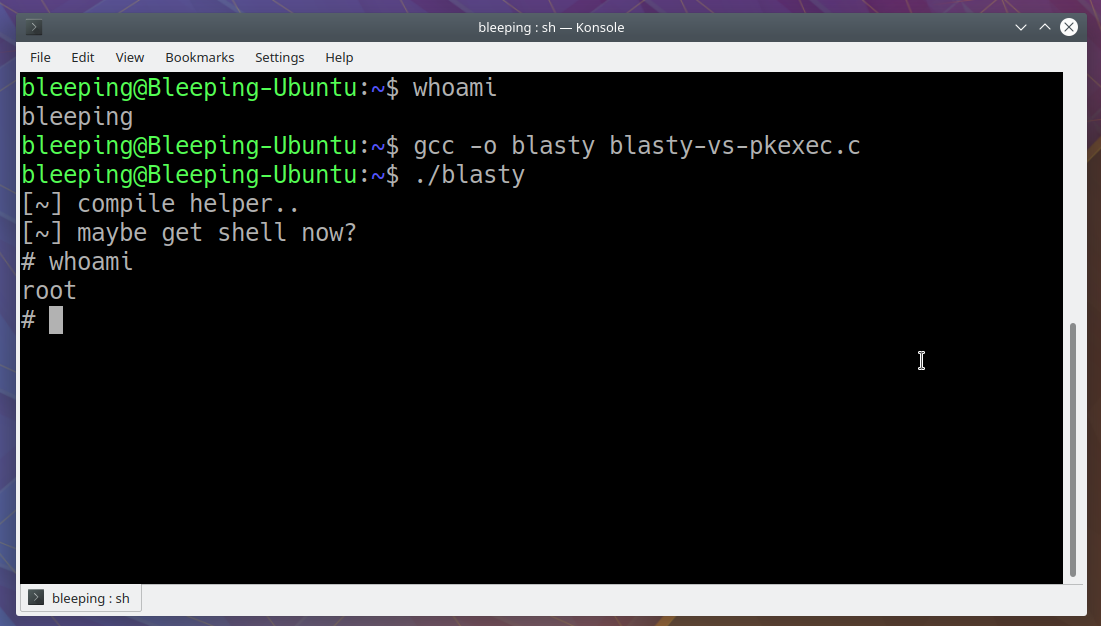
Referrinng to the exploit, CERT/CC vulnerability analyst Will Dormann said that it is each very simple and universal. The researcher further examined it on an ARM64 program, exhibiting that it operates on that architecture, as well.
Qualys described the safety challenge responsibly on November 18, 2021, and waited for a patch to turn into available ahead of publishing the technological information driving PwnKit.
The firm strongly endorses directors prioritize applying the patches that Polkit’s authors unveiled on their GitLab a couple of hrs ago.
Linux distros experienced entry to the patch a few of weeks ahead of today’s coordinated disclosure from Qualys and are anticipated to launch up-to-date pkexec offers commencing currently.
Ubuntu has currently pushed updates for PolicyKit to tackle the vulnerability in versions 14.04 and 16.04 ESM (extended security routine maintenance) as properly as in additional new versions 18.04, 20.04, and 21.04. Buyers just want to operate a standard process update and then reboot the pc for the variations to take influence.
Purple Hat has also shipped a security update for polkit on Workstation and on Organization products and solutions for supported architectures, as well as for extended existence cycle assist, TUS, and AUS.
A short term mitigation for functioning devices that have yet to press a patch is to use the adhering to command to strip pkexec of the setuid bit:
chmod 0755 /usr/bin/pkexecPeople that want to glimpse for signals of PwnKit exploitation can do it by examining the logs for possibly “The worth for the SHELL variable was not found the /and so on/shells file” or “The benefit for surroundings variable […] is made up of suspicious written content.” entries.
Nevertheless, Qualys notes that exploiting PwnKit is probable with no leaving a trace.
Previous 12 months, GitHub Protection Lab researcher Kevin Backhouse found an additional old privilege escalation vulnerability affecting Polkit.
The bug experienced been existing for seven decades, since model .113 of the ingredient and affected popular Linux distros together with RHEL 8, Fedora 21 (or later), Ubuntu 20.04, and unstable variations of Debian (‘bullseye’) and its derivatives.
Update [January 25, 17:26 EST]: Additional protection notices on PolicyKit / Polkit from Ubuntu and Red Hat.
Update [January 25, 17:43 EST]: Short article up to date with data about evidence-of-principle exploit code getting publicly available.